Context labels



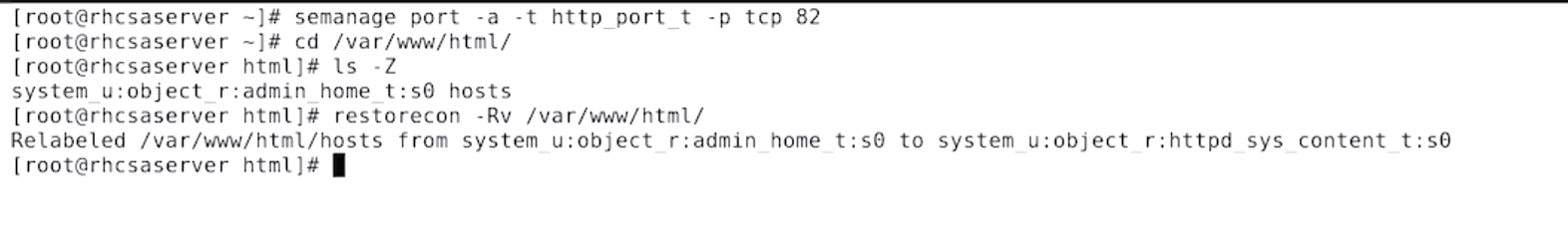
restorecon
- you can use
restorecon -Rv <directory>to restore it to the default contexts. - these default contexts are stores in
/etc/selinux/targeted/contexts/files/ restoreconwill compare the current context with the default context and restore them.

fcontext

semanage fcontextwrites to the policy. not to the inode. to enforce policy setting on the file system you have to userestorecon
Changing the httpd root directory
Finding the right context

dnf search selinuxin the exam you might have a hard time finding the exact name of the package. that’s why we use above command.

dnf install -y selinux-policy-docman -k _selinuxman -k _selinux | grep httpd
man httpd_selinux
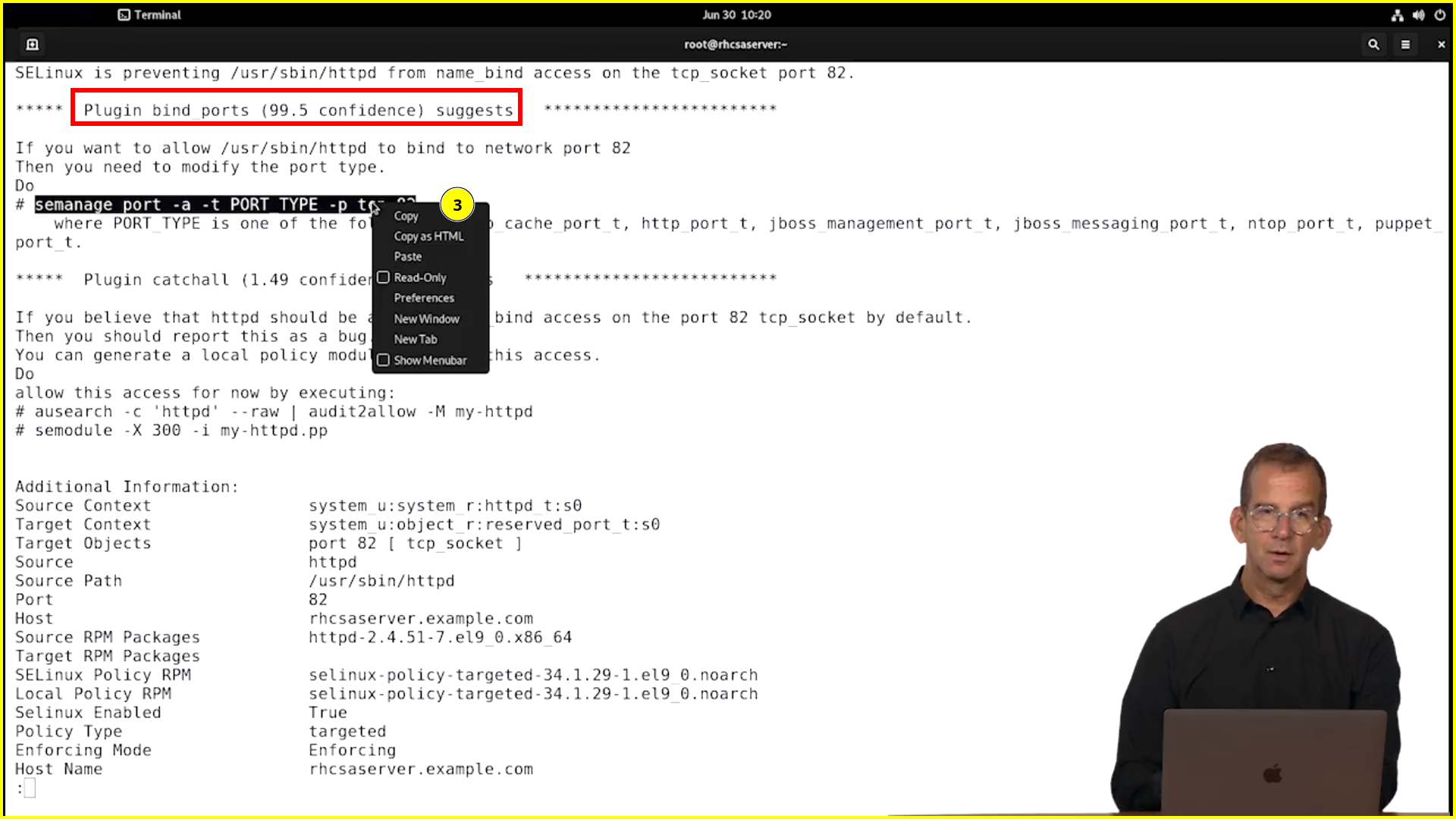
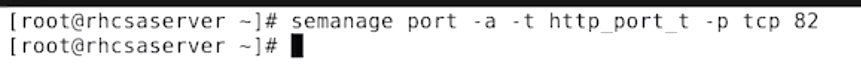
SELinux Port


Demo - change ssh port









if you get an error message saying context is already assigned. then you have to use -m instead of -a

SELinux Boolean




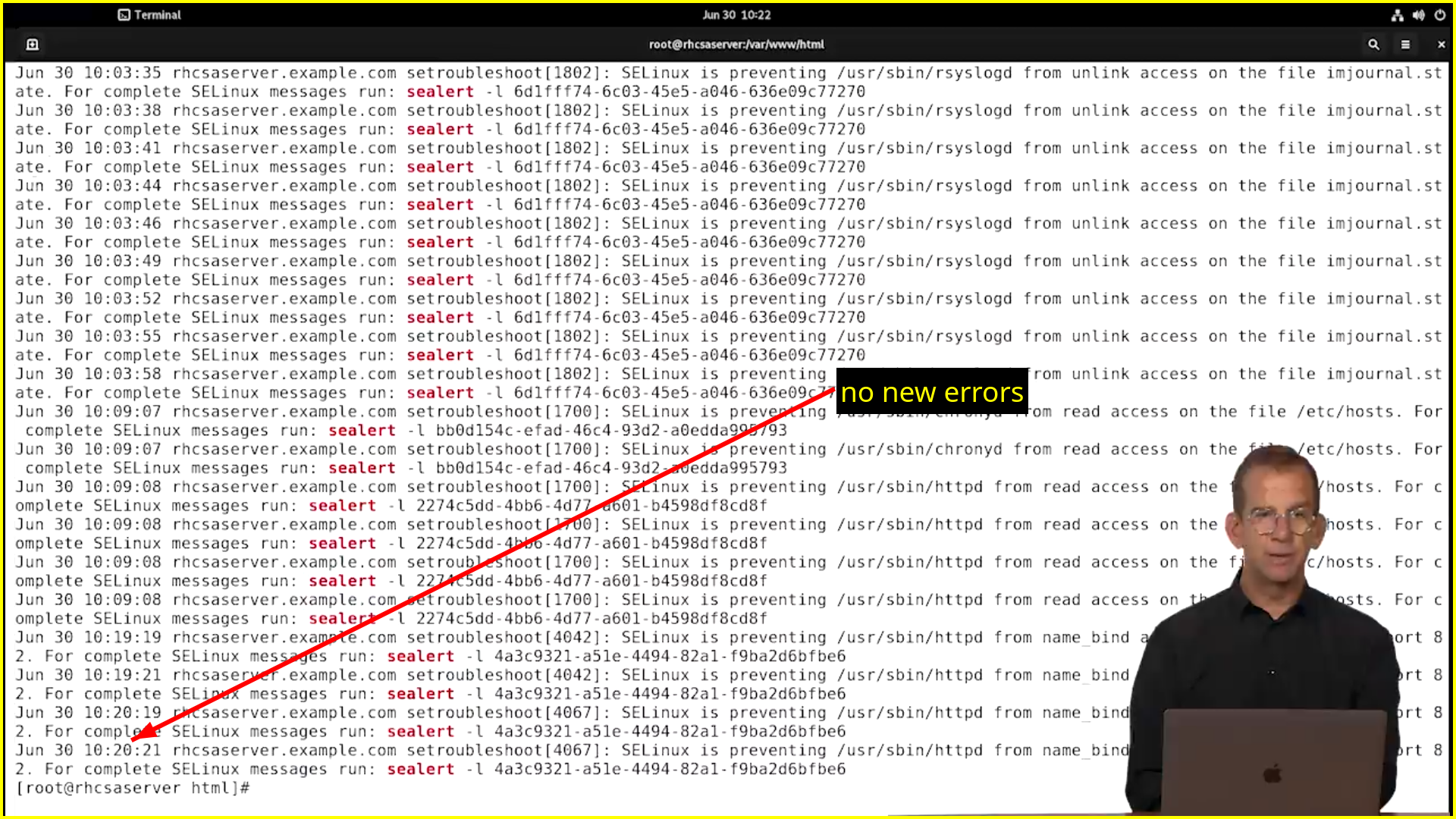
SELinux log messages

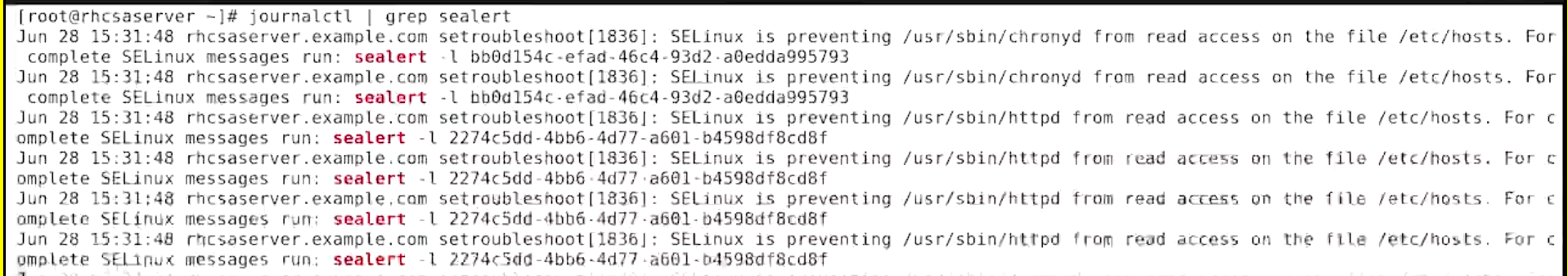
journalctl | grep sealert





-
autorelabel is not harmful in anycase. you can do it anytime. that’s why we are doing it without worrying much
-
its normal if your system reboot more than once in an autorelabelling action
-
autorebelling keep rebooting(5 times, that doesn’t make sense, something is wrong).
-
you have to change the grub
systemd.unit=emergency.target
ls -l /in the error messages you have seen something about read only file system. so it can’t remove the /.autorelabel file. that’s why its keep rebooting

see our assumption is right
mount -o remount,rw /
if autorelabelling is failing then we have to relabel manually
restorecon -Rv / you have to wait untill this is done. then you have to restart again.
you have to wait untill this is done. then you have to restart again.
Troubleshooting SELinux

setenforce 0
grep AVC /var/log/audit/audit.log
dnf install selinux-policy-doc
journalctl | grep sealert
try to avoid selinux-policy-doc in the exam. because you will be overwhelmed by the amount of information in there